适用于:Azure 本地 2509 及更高版本
本文介绍如何为 Azure Arc 启用的 Azure 本地虚拟机(VM)启用受信任启动的来宾证明。来宾证明(也称为启动完整性验证)是一项新功能,可以从 Azure 本地版本 2509 开始预览。
客户机证明允许您验证虚拟机 (VM) 是否以已知的良好状态启动——具体而言,验证整个启动链的完整性。 这有助于检测启动链(固件、OS 启动加载程序和驱动程序)的任何意外更改,以便在启动链遭到入侵时采取纠正措施。
启用来宾证明时,会在 VM 上部署一个名为来宾证明扩展的 Azure Arc 扩展。 来宾证明扩展与 Azure 服务(例如Microsoft Azure 证明服务)交互,以支持启动完整性验证。
先决条件
Azure 本地实例必须运行版本 2509 或更高版本。
将
Microsoft.Attestation资源提供程序注册到您的订阅,请参阅 向 Azure Arc 注册 Azure 本地计算机并分配部署权限。 在设置新的 Azure 本地实例或更新现有 Azure 本地实例之前,必须执行此作。 每个订阅只需执行一次。
使用 Azure 门户启用来宾验证
通过 Azure 门户创建可信启动 Azure 本地虚拟机时,可以启用来宾验证。
有关通过 Azure 门户创建启用 Azure Arc 的受信任启动 Azure 本地虚拟机的一般说明,请参阅 创建启用 Azure Arc 的 Azure 本地虚拟机。
注释
创建 VM 时指定网络接口。 受信任的启动需要网络连接以进行证明。
创建 VM 时,选择安全类型作为 受信任的启动。
选择“配置安全功能”,然后选择“完整性监视”(预览版)。
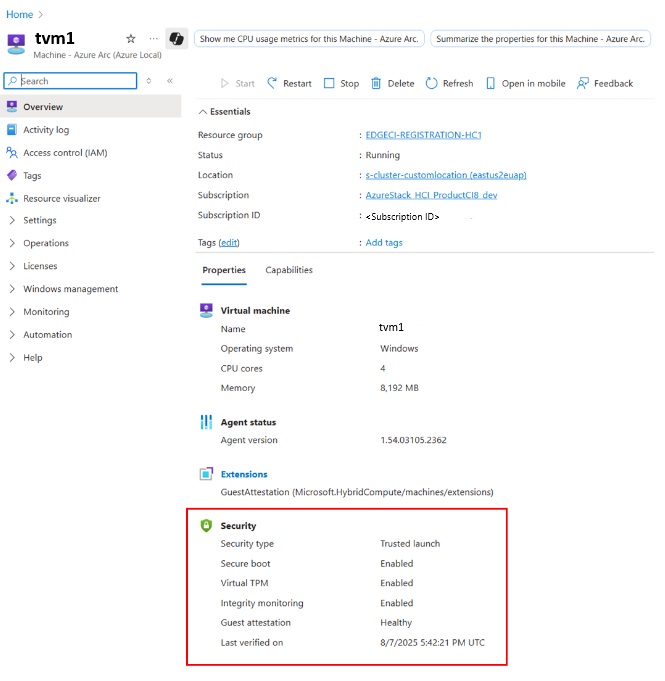
创建虚拟机后,可以通过虚拟机资源页查看客户机证明状态。
访客认证状态 Meaning 正常 已启用安全启动,启用了虚拟 TPM,并且启动完整性验证成功。 Unhealthy 未启用安全启动,或者未启用虚拟 TPM,或者启动完整性监视未成功。 未知 由于暂时性网络或通信问题,状态不可用。 时间戳显示上次验证来宾证明状态的时间。 状态通常每隔 8 小时刷新一次。 如果 VM 处于运行状态,但来宾证明状态在 8 个多小时内未更新,这可能是因为来宾证明扩展停止工作,或者 VM 可能已泄露。
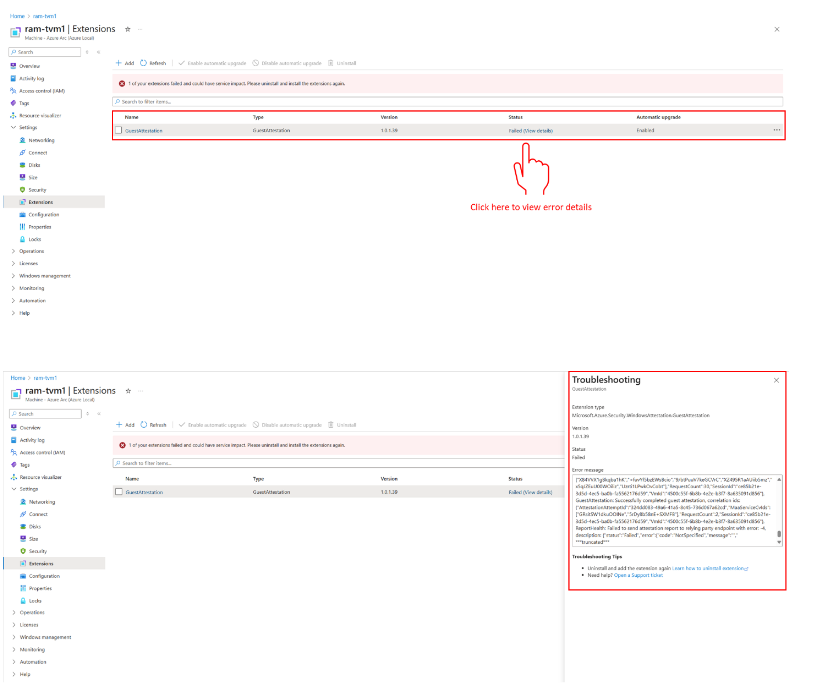
可以在扩展页查看来宾证明扩展功能的状态。
如果来宾证明扩展的状态报告为 “失败”,可以查看详细的错误状态:
使用 Azure CLI 启用来宾验证
创建受信任的启动 VM
有关通过 Azure CLI 创建受信任启动的 Azure Arc 启用的本地 Azure 虚拟机的一般说明,请参阅 创建由 Azure Arc 启用的本地 Azure 虚拟机。
安装 Azure Arc 客户机验证扩展
按如下所示构造扩展设置:
- 证明服务终结点
- 信赖方服务终结点
- 群集 ID
- Azure Active Directory (AAD) 租户 ID
注释
扩展设置区分大小写。
下面是一个示例:
# To connect to your Azure Local via Az CLI, see https://free.blessedness.top/en-us/azure/azure-local/azure-arc-vm-management-prerequisites.md?#azure-command-line-interface-cli-requirements. # Login to Azure [host1]: PS C:\Users\HCIDeploymentUser> az login --use-device-code # Set your subscription [host 1]: PS C:\Users\HCIDeploymentUser> az account set --subscription "<subscription>" [host1]: PS C:\Users\HCIDeploymentUser> $cluster = (az stack-hci cluster show --subscription "<subscription>" --resource-group "<resource group>" --name "<Azure Local instance name>") | ConvertFrom-Json [host1]: PS C:\Users\HCIDeploymentUser> $extensionSettings= '"{\"AttestationConfig\":{\"MaaSettings\":{\"maaEndpoint\": \"' + $cluster.isolatedVmAttestationConfiguration.attestationServiceEndpoint + '\",\"maaTenantName\": \"DUMMY_Tenant_NewConfig\"},\"AscSettings\":{\"ascReportingEndpoint\": \"' + $cluster.isolatedVmAttestationConfiguration.relyingPartyServiceEndpoint + '\",\"ascReportingFrequency\": \"4H\"},\"AzureStackSettings\":{\"clusterId\": \"'+$cluster.id+'\",\"clusterAadTenantId\": \"'+$cluster.aadTenantId+'\"},\"useCustomToken\": \"true\",\"disableAlerts\": \"false\",\"isAzureStack\": \"true\"}}"'部署 Azure Arc 来宾证明扩展,如以下示例所示:
# Check if "connectedmachine" extension is already installed. If it is installed, it should be in the extensions list in the output of the command below. [host1]: PS C:\Users\HCIDeploymentUser> az version { "azure-cli": "2.60.0", "azure-cli-core": "2.60.0", "azure-cli-telemetry": "1.1.0", "extensions": { "aksarc": "1.2.20", "arcappliance": "1.1.1", "connectedk8s": "1.6.2", "customlocation": "0.1.3", "k8s-extension": "1.4.5", "stack-hci-vm": "1.1.11" } } # if "connectedmachine" extension is not already installed, add "connectedmachine" extension. [host1]: PS C:\Users\HCIDeploymentUser> az extension add --name connectedmachine az : WARNING: Default enabled including preview versions for extension installation now. Disabled in May 2024. Use '--allow-preview true' to enable it specifically if needed. Use '--allow-preview false' to install stable version only. + CategoryInfo : NotSpecified: (WARNING: Defaul... version only. :String) [], RemoteException + FullyQualifiedErrorId : NativeCommandError WARNING: The installed extension 'connectedmachine' is in preview. # Run the command below to install the Azure Arc guest attestation extension. [host1]: PS C:\Users\HCIDeploymentUser> az connectedmachine extension create --subscription "<subscription>" --resource-group "<resource group>" --machine-name "<name of VM>" --location "<Azure region of your Azure Local instance>" --publisher "Microsoft.Azure.Security.WindowsAttestation" --type "GuestAttestation" --name "GuestAttestation" --settings $extensionSettings --enable-automatic-upgrade { "id": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.HybridCompute/machines/myTVM/extensions/GuestAttestation", "location": "eastus", "name": "GuestAttestation", "properties": { "autoUpgradeMinorVersion": false, "enableAutomaticUpgrade": true, "instanceView": { "name": "GuestAttestation", "status": { "code": "0", "level": "Information", "message": "Extension Message: Command: None, Status: has successfully completed. Details: [ Running Extension:GuestAttestation Operation:None ], Enable: Starting Enabling Step., Enable: Starting Client. Details: AszAttestationClient -a https://clustxxxxxxxxxx.eus2e.attest.azure.net -r https://dp.stackhci.azure.com/eastus/igvmAttestation/validxxxxx -l C:\\ProgramData\\GuestConfig\\extension_logs\\Microsoft.Azure.Security.WindowsAttestation.GuestAttestation -h C:\\Packages\\Plugins\\Microsoft.Azure.Security.WindowsAttestation.GuestAttestation\\1.0.1.30\\status\\HeartBeat.Json -s C:\\Packages\\Plugins\\Microsoft.Azure.Security.WindowsAttestation.GuestAttestation\\1.0.1.30\\status\\0.status -e events -v 1.0.1.30 -c /subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.AzureStackHCI/clusters/<cluster name> -d xxxxxxxx--a9d3-41ba-88c3-796a643e3edd, Enable: Client : AszAttestationClient Started Successfully" }, "type": "GuestAttestation", "typeHandlerVersion": "1.0.1.30" }, "provisioningState": "Succeeded", "publisher": "Microsoft.Azure.Security.WindowsAttestation", "settings": { "AttestationConfig": { "AscSettings": { "ascReportingEndpoint": "https://dp.stackhci.azure.com/eastus/igvmAttestation/validxxxxx", "ascReportingFrequency": "4H" }, "AzureStackSettings": { "clusterAadTenantId": "xxxxxxxx--a9d3-41ba-88c3-796a643e3edd", "clusterId": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.AzureStackHCI/clusters/<cluster name>" }, "MaaSettings": { "maaEndpoint": "https://clustxxxxxxxxxxxxx.eus2e.attest.azure.net", "maaTenantName": "My_Tenant_NewConfig" }, "disableAlerts": "false", "isAzureStack": "true", "useCustomToken": "true" } }, "type": "GuestAttestation", "typeHandlerVersion": "1.0.1.30" }, "resourceGroup": "<resource group name>", "type": "Microsoft.HybridCompute/machines/extensions" }
查看来宾认证状态
可以使用 Azure CLI 查看来宾证明状态。 来宾证明状态由输出中的以下属性列出:
"attestSecureBootEnabled": "Enabled","attestationCertValidated": "Valid","bootIntegrityValidated": "Valid","errorMessage": null,"healthStatus": "Healthy","linuxKernelVersion": "0","provisioningState": "Succeeded",
下面是 Az CLI 命令和示例输出:
# To connect to your Azure Local via Az CLI, see https://free.blessedness.top/en-us/azure/azure-local/azure-arc-vm-management-prerequisites.md?#azure-command-line-interface-cli-requirements.
# Login to Azure
PS C:\WINDOWS\system32>az login --use-device-code
# Set your subscription
[host 1]: PS C:\Users\HCIDeploymentUser> az account set --subscription "<subscription>"
# Get list of installed extensions
PS C:\WINDOWS\system32>az version
{
"azure-cli": "2.61.0",
"azure-cli-core": "2.61.0",
"azure-cli-telemetry": "1.1.0",
"extensions": {
"azure-iot": "0.11.0",
"stack-hci-vm": "1.1.11"
}
}
# If “stack-hci-vm” extension version isn't “1.1.12” or above, install the latest version of the extension.
PS C:\WINDOWS\system32>az extension remove --name stack-hci-vm
PS C:\WINDOWS\system32>az extension add --name stack-hci-vm
PS C:\WINDOWS\system32>az version
{
"azure-cli": "2.61.0",
"azure-cli-core": "2.61.0",
"azure-cli-telemetry": "1.1.0",
"extensions": {
"azure-iot": "0.11.0",
"stack-hci-vm": "1.1.14"
}
}
# Check guest attestation status.
PS C:\WINDOWS\system32> az stack-hci-vm show --subscription "<subscription id>" --resource-group "<resource group name>" --name "<name of VM>"
Command group 'stack-hci-vm' is experimental and under development. Reference and support levels: https://aka.ms/CLI_refstatus
{
"attestationStatus": {
"id": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.HybridCompute/machines/<vm name>/providers/Microsoft.AzureStackHCI/virtualMachineInstances/default/AttestationStatus/default",
"name": "default",
"properties": {
"attestSecureBootEnabled": "Enabled",
"attestationCertValidated": "Valid",
"bootIntegrityValidated": "Valid",
"errorMessage": null,
"healthStatus": "Healthy",
"linuxKernelVersion": "0",
"provisioningState": "Succeeded",
"timestamp": "6/12/2024 8:49:33 PM"
},
"resourceGroup": "<resource group name>",
"systemData": {
"createdAt": "2024-06-12T20:49:33.545606+00:00",
"createdBy": "1412d89f-b8a8-4111-b4fd-e82905cbd85d",
"createdByType": "Application",
"lastModifiedAt": "2024-06-12T20:49:33.545606+00:00",
"lastModifiedBy": "1412d89f-b8a8-4111-b4fd-e82905cbd85d",
"lastModifiedByType": "Application"
},
"type": "microsoft.azurestackhci/virtualmachineinstances/attestationstatus"
},
"virtualmachineinstance": {
"extendedLocation": {
"name": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.ExtendedLocation/customLocations/cluster-customlocation",
"type": "CustomLocation"
},
"id": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.HybridCompute/machines/myTVM/providers/Microsoft.AzureStackHCI/virtualMachineInstances/default",
"identity": null,
"name": "default",
"properties": {
"guestAgentInstallStatus": null,
"hardwareProfile": {
"dynamicMemoryConfig": {
"maximumMemoryMb": null,
"minimumMemoryMb": null,
"targetMemoryBuffer": null
},
"memoryMb": 2048,
"processors": 4,
"vmSize": "Custom"
},
"httpProxyConfig": null,
"instanceView": {
"vmAgent": {
"statuses": [
{
"code": "ProvisioningState/succeeded",
"displayStatus": "Connected",
"level": "Info",
"message": "Successfully established connection with mocguestagent",
"time": "2024-06-12T20:10:37+00:00"
},
{
"code": "ProvisioningState/succeeded",
"displayStatus": "Connected",
"level": "Info",
"message": "New mocguestagent version detected 'v0.14.0-2-g5c6a4b32'",
"time": "2024-06-12T20:10:36+00:00"
}
],
"vmConfigAgentVersion": "v0.14.0-2-g5c6a4b32"
}
},
"isHydration": null,
"networkProfile": {
"networkInterfaces": [
{
"id": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.AzureStackHCI/networkinterfaces/my-nic-static",
"resourceGroup": "<resource group name>"
}
]
},
"osProfile": {
"adminPassword": null,
"adminUsername": "<admin username>",
"computerName": "<computer name>",
"linuxConfiguration": {
"disablePasswordAuthentication": null,
"provisionVmAgent": true,
"provisionVmConfigAgent": true,
"ssh": {
"publicKeys": null
}
},
"windowsConfiguration": {
"enableAutomaticUpdates": null,
"provisionVmAgent": true,
"provisionVmConfigAgent": true,
"ssh": {
"publicKeys": null
},
"timeZone": null
}
},
"provisioningState": "Succeeded",
"resourceUid": null,
"securityProfile": {
"enableTpm": true,
"securityType": "TrustedLaunch",
"uefiSettings": {
"secureBootEnabled": true
}
},
"status": {
"errorCode": "",
"errorMessage": "",
"powerState": "Running",
"provisioningStatus": null
},
"storageProfile": {
"dataDisks": [],
"imageReference": {
"id": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/microsoft.azurestackhci/marketplacegalleryimages/Win11EntMulti23H2",
"resourceGroup": "<resource group name>"
},
"osDisk": {
"id": null,
"osType": "Windows"
},
"vmConfigStoragePathId": "/subscriptions/<subscription id>/resourceGroups/<resource group name>/providers/Microsoft.AzureStackHCI/storagecontainers/UserStorage2-7d0fdc06e3ef4c9d808ceb31379d0916" },
"vmId": "85b8849e-2965-4c82-b7fa-637796d22199"
},
"resourceGroup": "<resource group name>",
"systemData": {
"createdAt": "2024-06-12T20:03:18.171067+00:00",
"createdBy": "69be5a28-cb3c-4916-98c3-7e4ab37a83e0",
"createdByType": "Application",
"lastModifiedAt": "2024-06-12T20:11:55.649002+00:00",
"lastModifiedBy": "319f651f-7ddb-4fc6-9857-7aef9250bd05",
"lastModifiedByType": "Application"
},
"type": "microsoft.azurestackhci/virtualmachineinstances"
}
}
Guidance
来宾证明支持依赖于并使用 Microsoft Azure 证明服务。 支持来宾证明时,会自动将 Azure 本地实例设置为包含 Microsoft Azure 证明服务终结点和证明策略。 若要让来宾证明功能正常运行,需要提供对 Microsoft Azure 证明服务的出站网络访问权限。 确保 Azure 本地实例的相关策略或网络防火墙规则允许出站网络访问 Microsoft Azure 证明服务。
例如,使用 Azure Policy 管理 Azure 本地实例的安全状况时,不应禁止资源类型
Microsoft.Attestation/attestationProviders。 有关详细信息,请参阅 禁止云环境中的资源类型。 具体而言,必须启用策略Microsoft.Attestation/attestationProviders/publicNetworkAccess。有时,可能需要手动为 Azure 本地实例设置Microsoft Azure 证明服务终结点和关联的证明策略。 例如,可能会意外从 Azure 本地实例的资源组中删除证明提供程序(和相关证明策略)。 另一个示例是,需要更新证明策略,以使用预配到 Azure 本地实例的不同证明根证书。
在这种情况下,可以运行以下命令,手动为 Azure 本地实例设置Microsoft Azure 证明服务终结点和证明策略。 以下命令必须从 Azure 本地实例中的一台计算机(节点)运行。
$ececlient = create-ececlusterserviceclient
# Create MAA Endpoint
$guid= Invoke-ActionPlanInstance -RolePath Cloud\Infrastructure\ArcIntegration -ActionType "CreateMAAEndpointCloud" -EceClient $ececlient
# Validate MAA Endpoint creation succeeded
Get-ActionPlanInstance -ActionPlanInstanceId $guid -ececlient:$ececlient
# Create MAA Policy
$guid= Invoke-ActionPlanInstance -RolePath Cloud\Infrastructure\ArcIntegration -ActionType "CreateMAAPolicyCloud" -EceClient $ececlient
# Validate MAA Policy creation succeeded
Get-ActionPlanInstance -ActionPlanInstanceId $guid -ececlient:$ececlient
# Sample expected output
# InstanceID: <guid>
# ActionPlanName:
# ActionTypeName: CreateMAAEndpointCloud
# RolePath: Cloud\Infrastructure\ArcIntegration
# ProgressAsXml: <xml-object>
# Status: Completed
# ...