Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Some information relates to prereleased product that may be substantially modified before it's commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
The hunting graph provides visualization capabilities in advanced hunting by rendering threat scenarios as interactive graphs. This feature allows security operations center (SOC) analysts, threat hunters, and security researchers conduct threat hunting and incident response easily and more intuitively, improving their efficiency and ability to assess possible security issues.
Analysts often rely on Kusto Query Language (KQL) queries to uncover relationships between entities—an approach that could be both time-consuming and prone to oversights. Hunting graph makes exploration of security data simpler and faster by visualizing these relationships, letting you trace paths and possible choke points, as well as surface insights and take various actions based on the results that tabular queries might miss.
Get access
To use hunting graph, advanced hunting, or other Microsoft Defender XDR capabilities, you need an appropriate role in Microsoft Entra ID. Read about required roles and permissions for advanced hunting.
You must also have the following access or permissions:
- Microsoft Sentinel data lake
- At least read-only access in Microsoft Security Exposure Management
Where to find hunting graph
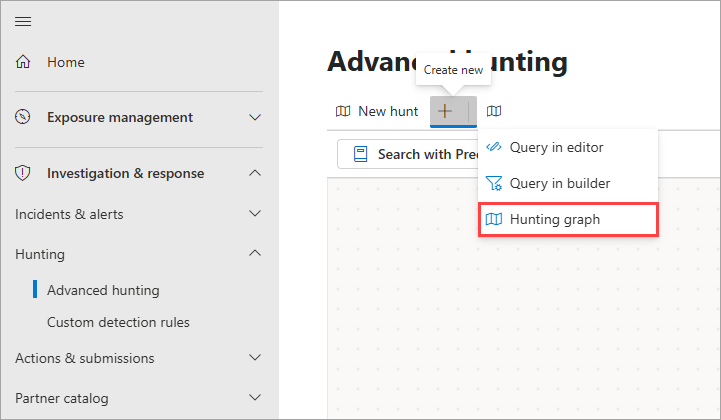
You can find the hunting graph page by going to the left navigation bar in the Microsoft Defender portal and selecting Investigation & response > Hunting > Advanced hunting.
In the advanced hunting page, select the hunting graph icon ![]() at the top of the page or select the Create new icon
at the top of the page or select the Create new icon ![]() and choose Hunting graph.
and choose Hunting graph.
A new hunting graph page appears as tab labeled New hunt in the advanced hunting page.
Hunting graph features
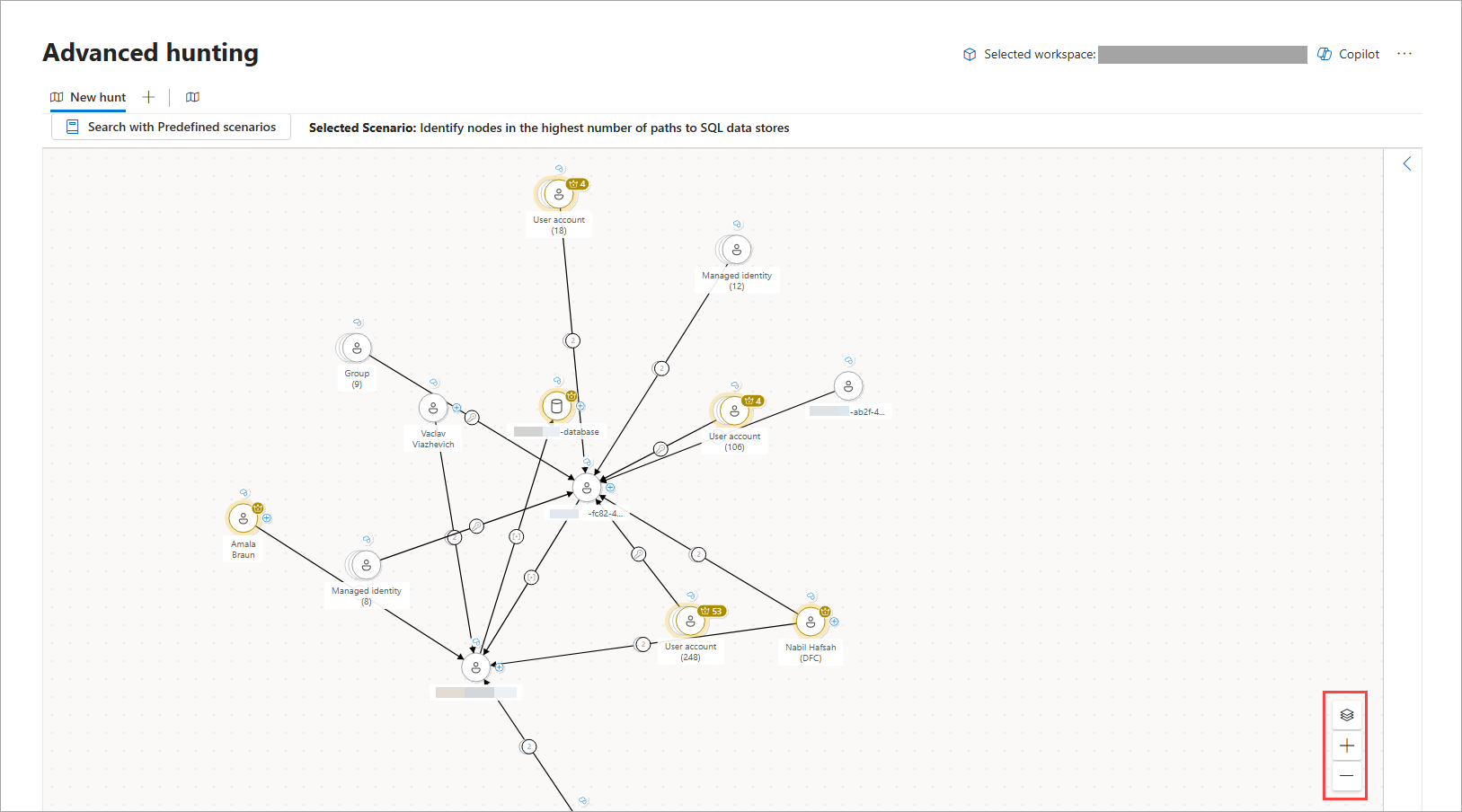
The interactive graphs generated in the hunting graph are composed of nodes and edges to represent entities in your environment (for example, a device, user account, or IP address, among others) and their relationships or connection properties, respectively. Learn more about graphs and visualizations in Microsoft Defender
The lower right-hand corner of the graph also has control buttons that let you Zoom in and Zoom out, and view the graph's Layers.
Get started with hunting graph
Use predefined scenarios in the hunting graph
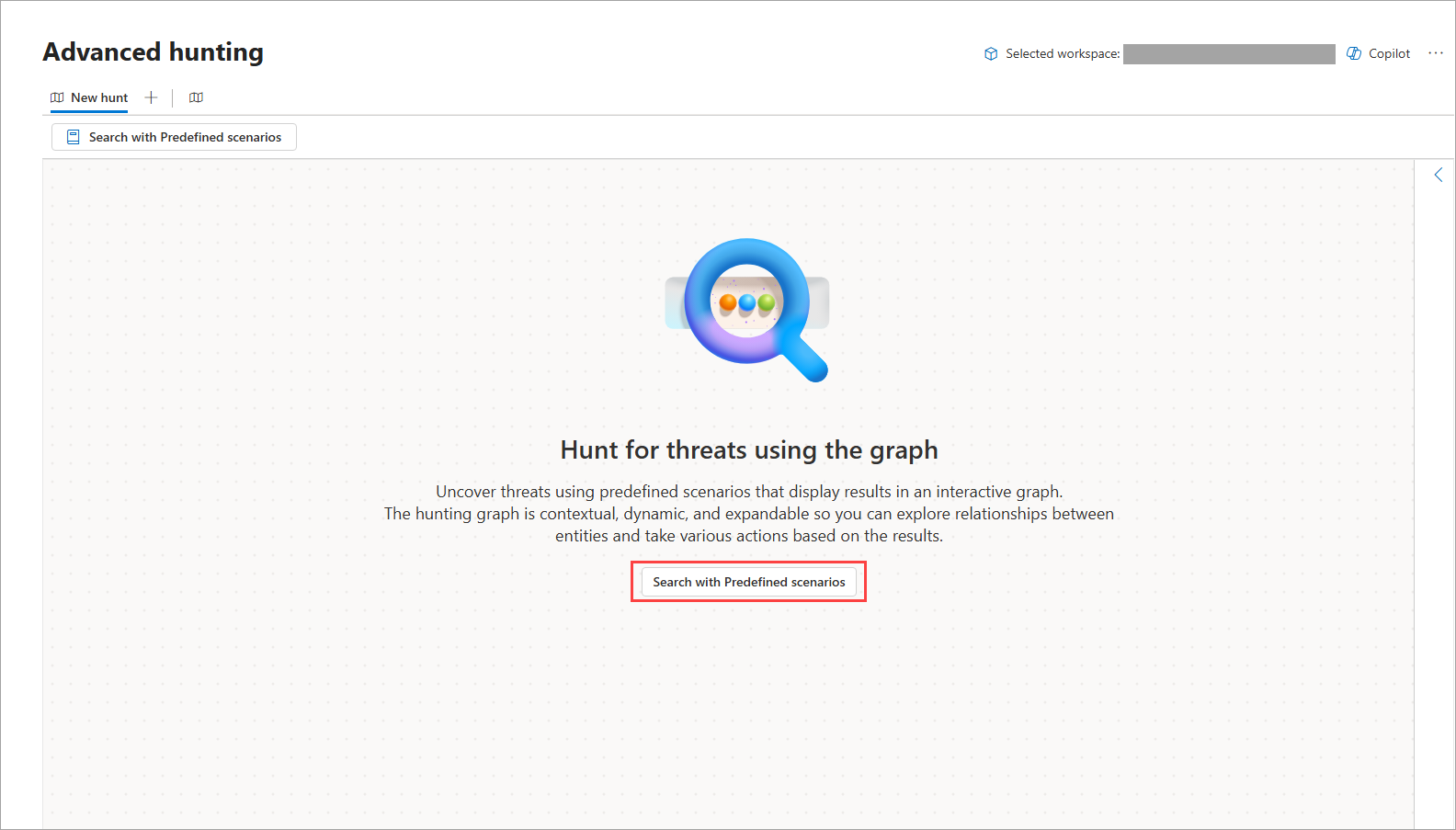
The hunting graph lets you search with predefined scenarios, which are prebuilt advanced hunting queries that could help you answer specific and common questions for specific use cases.
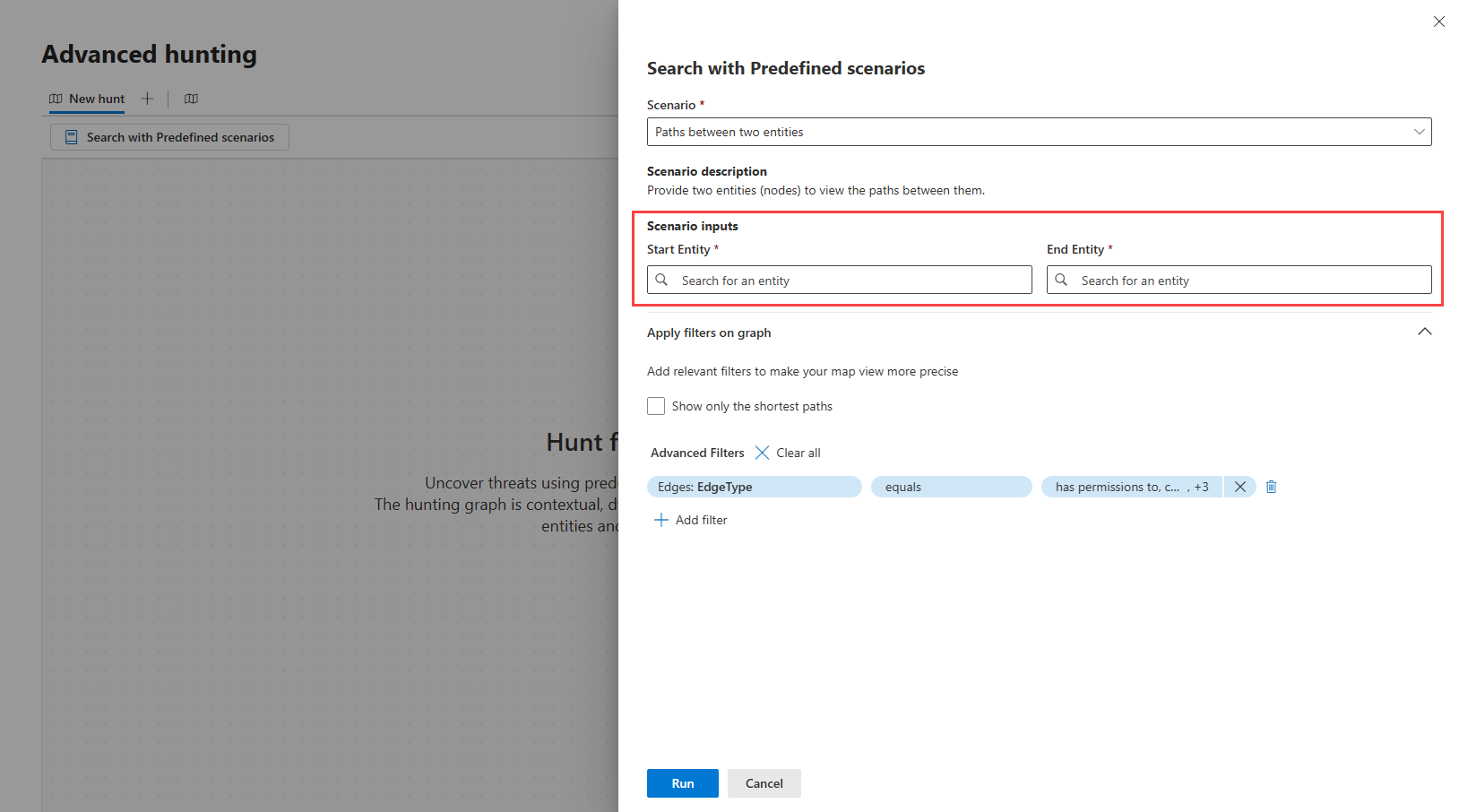
To start hunting using a predefined scenario, on a new hunting graph page, select Search with Predefined scenarios. A side panel appears where you can then perform the following steps:
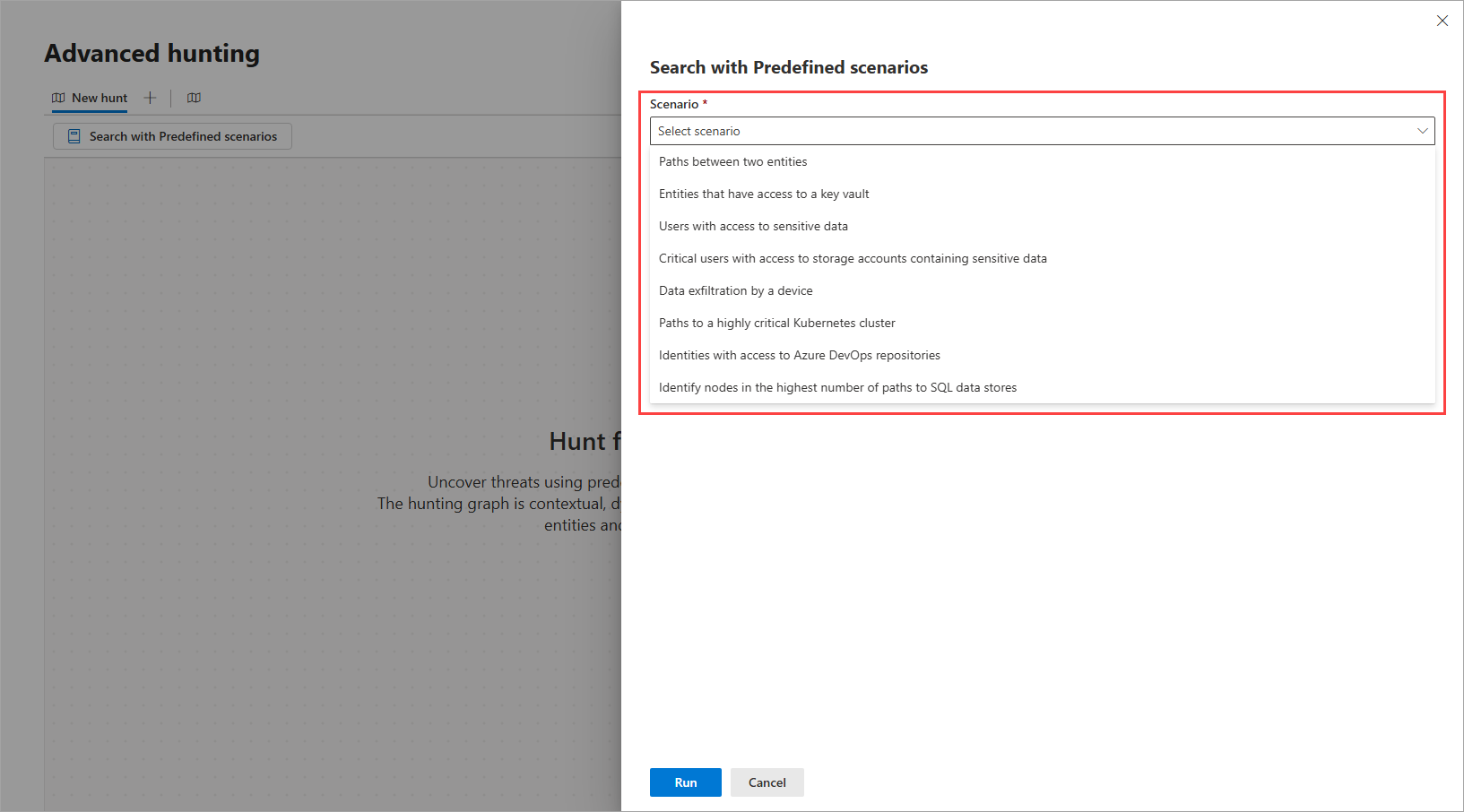
Step 1: Select a scenario and enter scenario inputs
The following table describes the predefined scenarios in the hunting graph and their respective required scenario inputs, if applicable. For scenarios that require inputs, you can type or search and select for them in the search boxes provided.
| Scenario | Description | Inputs |
|---|---|---|
| Paths between two entities | Provide two entities (nodes) to view the paths between them. Use this scenario if you want to discover if there’s a path leading from one entity to another. |
|
| Entities that have access to a key vault | Provide a specific key vault to view paths from various entities (devices, virtual machines, containers, servers, and others) that have direct or indirect access to it. Use this scenario in case of a breach, maintenance work, or assessment of the impact of entities that might have access to a sensitive asset like a key vault. |
Target key vault |
| Users with access to sensitive data | Provide any sensitive data storage of interest to view users that have access to it. Use this scenario if you want to know which entities have access to sensitive data, especially in cases when an incident indicates unusual access to confidential files. |
Target storage account |
| Critical users with access to storage accounts containing sensitive data | This scenario identifies critical users with access to storage resources containing sensitive data. Use this scenario to prevent, assess, and monitor unauthorized access, exposure risk, and breach impact based on the privileged users. |
(None) |
| Data exfiltration by a device | Provide a device ID to view paths to storage accounts it has access to; for instance, to check what storage accounts a certain device can access in a bring your own device (BYOD) environment. Use this scenario when investigating suspicious or unauthorized data transfer from corporate devices and to external sources. |
Source device |
| Paths to a highly critical Kubernetes cluster | Provide a Kubernetes cluster with high criticality to view users, virtual machines, and containers that have access to it. Use this scenario to assess, analyze and prioritize handling of attack paths leading to highly critical Kubernetes cluster. |
Target Kubernetes cluster |
| Identities with access to Azure DevOps repositories | Provide an Azure DevOps (ADO) repository name to view users that have read and/or write access to said repository. Use this scenario to identify entities with access to ADO repositories, which often contain sensitive assets and therefore valuable targets for threat actors. This scenario gives you visibility and lets you plan your response in case of a breach. |
Target ADO repository |
| Identify nodes in the highest number of paths to SQL data stores | This scenario identifies the nodes that appear in the highest number of paths leading to SQL data stores. The scenario discovers paths in the graph where users have roles or permissions to access the SQL data stores. Use this scenario to gain visibility to stores that might contain sensitive information, assess the impact in case of a breach, and prepare your mitigation and response. |
(None) |
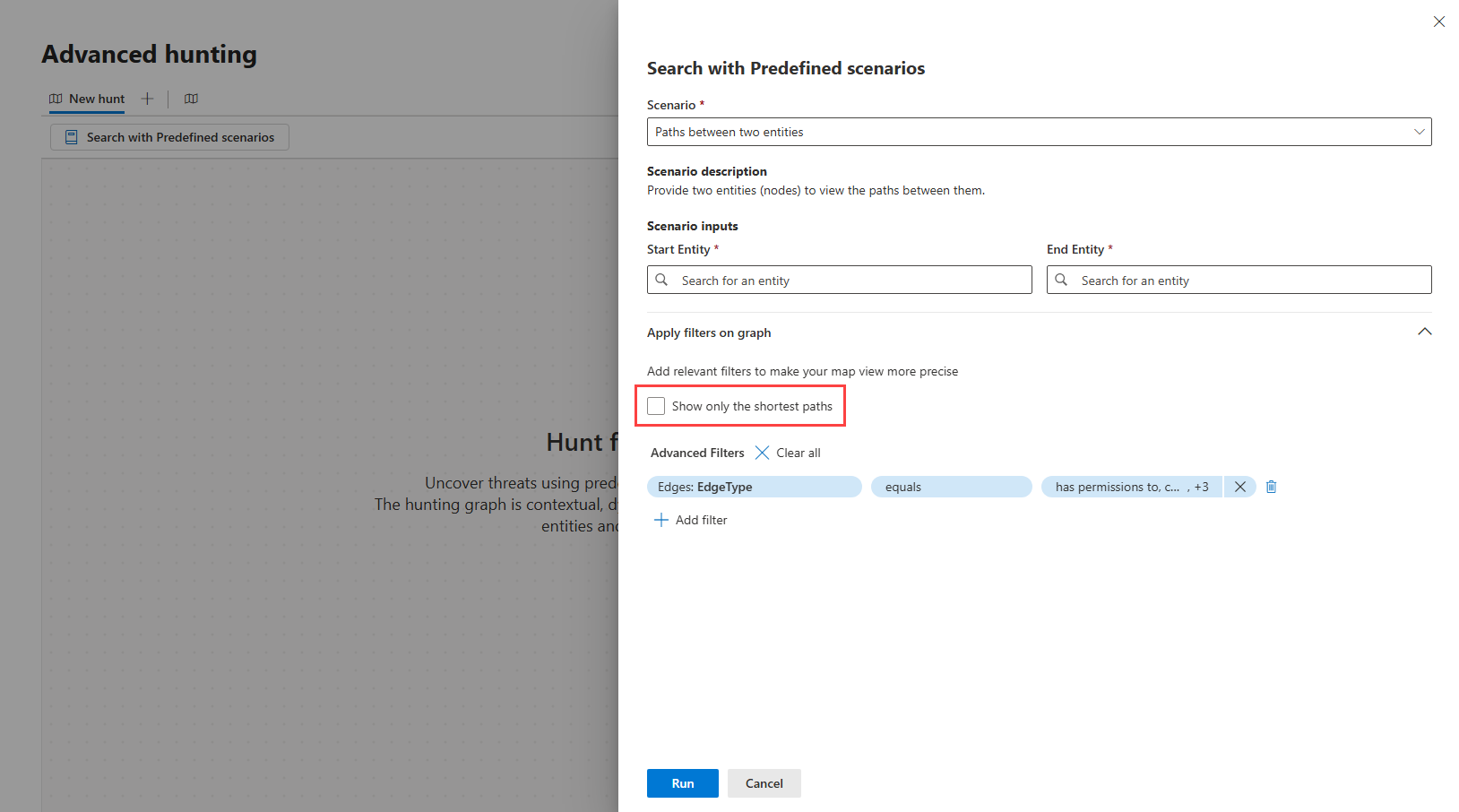
Step 2: Apply filters
You can add relevant filters to make the map view of your selected scenario more precise. For example, if you want to Show only the shortest paths, tick this option.
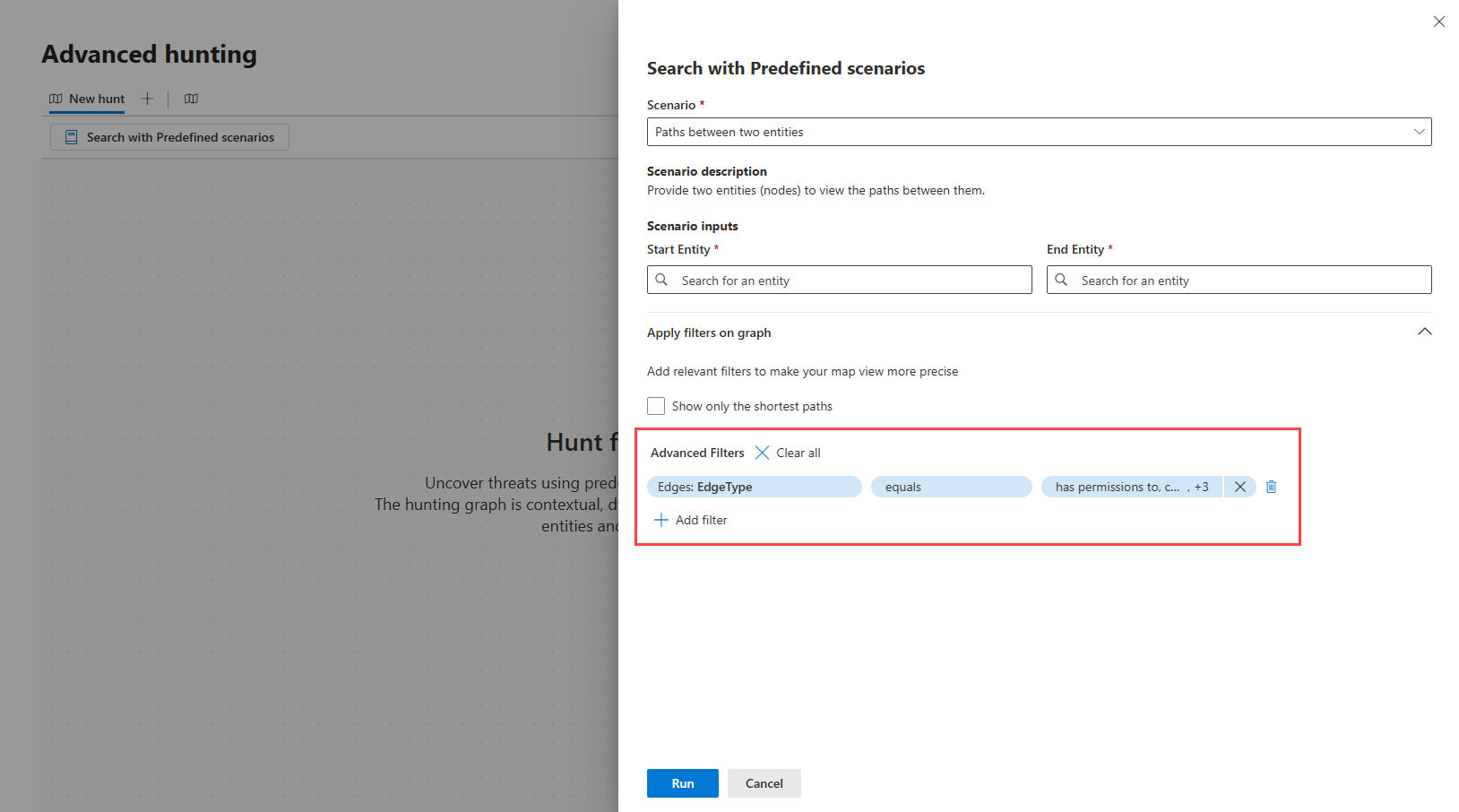
Advanced filters
By default, the predefined scenarios automatically apply certain filters, which you can view in the Advanced Filters section of the side panel. You can remove these filters or add new ones to further refine the graph you want to generate.
To remove filters, select the Remove filter icon ![]() beside each filter or select Clear all to remove them all at once.
beside each filter or select Clear all to remove them all at once.
To add a filter, select Add filter then the select any of the supported node or edge filters. The following table lists these supported operators and filters. Depending on your chosen scenario, some of these filters might not be available as options.
| Filter type | Operator | Filters |
|---|---|---|
| Source Node | equals |
|
| Target Node | equals |
|
| Edge Type | equals |
|
Step 3: Render the graph
After selecting a scenario and applying the necessary filters, select Run to render the graph. Once the graph is rendered, you can then explore it further by selecting nodes and edges to view more information about entities and relationships, or expand or focus on certain entities.