Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Get started with Service Connector to connect your Azure Kubernetes Service (AKS) cluster to databases, storage accounts, and other Azure services. Service Connector simplifies authentication and configuration, enabling you to connect to resources using a workload identity or other authentication methods.
This article provides step-by-step instructions for both the Azure portal and Azure CLI. Choose your preferred method using the tabs above.
Prerequisites
- An Azure account with an active subscription. Create an account for free.
- An AKS cluster in a region supported by Service Connector. If you don't have one yet, deploy an AKS cluster.
- The necessary permissions to create and manage service connections.
- An Azure account with an active subscription. Create an account for free.
- An AKS cluster in a region supported by Service Connector. If you don't have one yet, deploy an AKS cluster.
- The necessary permissions to create and manage service connections.
- An Azure Storage account. If you don't have one yet, create an Azure Storage account.
Use the Bash environment in Azure Cloud Shell. For more information, see Get started with Azure Cloud Shell.
If you prefer to run CLI reference commands locally, install the Azure CLI. If you're running on Windows or macOS, consider running Azure CLI in a Docker container. For more information, see How to run the Azure CLI in a Docker container.
If you're using a local installation, sign in to the Azure CLI by using the az login command. To finish the authentication process, follow the steps displayed in your terminal. For other sign-in options, see Authenticate to Azure using Azure CLI.
When you're prompted, install the Azure CLI extension on first use. For more information about extensions, see Use and manage extensions with the Azure CLI.
Run az version to find the version and dependent libraries that are installed. To upgrade to the latest version, run az upgrade.
- This quickstart requires version 2.30.0 or higher of the Azure CLI. To upgrade to the latest version, run
az upgrade. If using Azure Cloud Shell, the latest version is already installed.
Initial set-up
If you're using Service Connector for the first time, start by running the command az provider register to register the Service Connector and Kubernetes Configuration resource providers.
az provider register -n Microsoft.ServiceLinkeraz provider register -n Microsoft.KubernetesConfigurationTip
You can check if these resource providers have already been registered by running the commands
az provider show -n "Microsoft.ServiceLinker" --query registrationStateandaz provider show -n "Microsoft.KubernetesConfiguration" --query registrationState.Optionally, use the Azure CLI command to get a list of supported target services for AKS cluster.
az aks connection list-support-types --output table
Create a service connection in an AKS cluster
Use Service Connector to create a service connection between your Azure Kubernetes Service (AKS) cluster and Azure Blob Storage. This example demonstrates connecting to Blob Storage, but you can use the same process for other supported Azure services.
Select the Search resources, services and docs (G +/) search bar at the top of the Azure portal, type AKS, and select Kubernetes services.
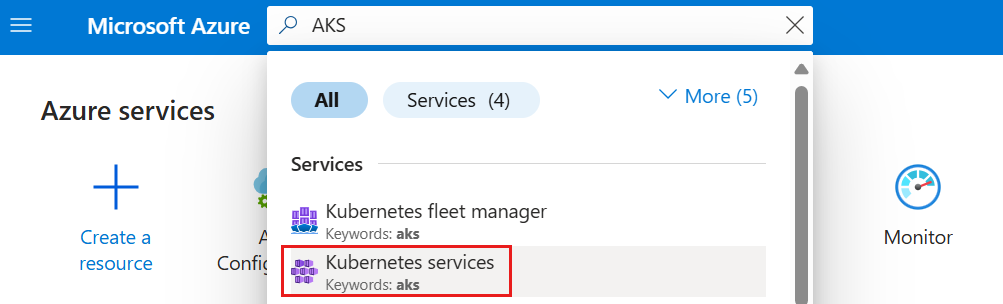
Select the AKS cluster you want to connect to a target resource.
Select Settings > Service Connector from the service menu. Then select Create.

On the Basics tab, select or enter the following settings.
Setting Example Description Kubernetes namespace default The namespace where you need the connection in the cluster. Service type Storage - Blob The target service type. If you don't have a Microsoft Blob Storage, you can create one or use another service type. Connection name my_connection The connection name that identifies the connection between your AKS cluster and target service. Use the connection name provided by Service Connector or choose your own connection name. Subscription My subscription The subscription for your target service (the service you want to connect to). The default value is the subscription for this AKS cluster. Storage account my_storage_account The target storage account you want to connect to. Target service instances to choose from vary according to the selected service type. Client type python The code language or framework you use to connect to the target service. Select Next: Authentication to choose an authentication method.
Select Workload identity to authenticate through Microsoft Entra workload identity to one or more instances of an Azure service. Then select a user-assigned managed identity to enable workload identity.
Select Next: Networking to configure the network access to your target service and select Configure firewall rules to enable access to your target service.
Note
Service Connector for AKS currently only supports the firewall option. Private link and service endpoint aren't supported.
Select Next: Review + Create to review the provided information. Then select Create to create the service connection. This operation might take a minute to complete.
Update your container
Now that you created a connection between your AKS cluster and target service, you need to retrieve the connection secrets and deploy them in your container.
In the Azure portal, navigate to your AKS cluster resource and go to Settings > Service Connector.
Select the newly created connection, and then select YAML snippet. This action opens a panel displaying a sample YAML file generated by Service Connector.
To set the connection secrets as environment variables in your container, you have two options:
Directly create a deployment using the YAML sample code snippet provided. The snippet includes highlighted sections showing the secret object that will be injected as the environment variables. Select Apply to proceed with this method.

Alternatively, under Resource Type, select Kubernetes Workload, and then select an existing Kubernetes workload. This action sets the secret object of your new connection as the environment variables for the selected workload. After selecting the workload, select Apply.

Run the az aks connection create storage-blob command. You can run this command in two different ways:
Generate the new connection step by step.
az aks connection create storage-blob \ --workload-identity <user-identity-resource-id>Generate the new connection at once. Replace the placeholders with your own information:
<source-subscription>,<source_resource_group>,<cluster>,<target-subscription>,<target_resource_group>,<account>, and<user-identity-resource-id>.az aks connection create storage-blob \ --source-id /subscriptions/<source-subscription>/resourceGroups/<source_resource_group>/providers/Microsoft.ContainerService/managedClusters/<cluster> \ --target-id /subscriptions/<target-subscription>/resourceGroups/<target_resource_group>/providers/Microsoft.Storage/storageAccounts/<account>/blobServices/default \ --workload-identity <user-identity-resource-id>
Tip
If you don't have a Blob Storage account, run az aks connection create storage-blob --new --workload-identity to create one and connect it to your App Service using a workload identity.
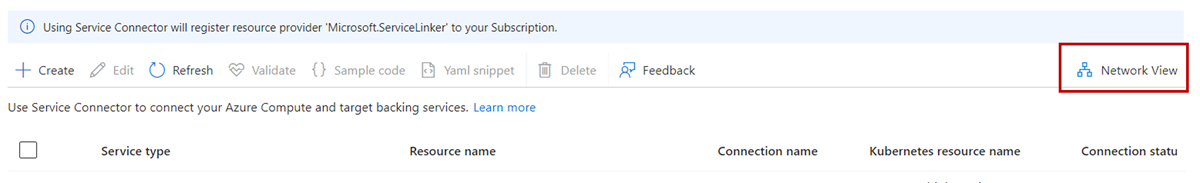
View service connections in AKS cluster
Service Connector displays existing connections in this cluster.
Select Network View to see all the service connections in a network topology view.
Run az aks connection list command to list all of your Azure Spring Apps' provisioned connections.
Replace the placeholders <cluster-resource-group>, and <cluster-name>, from the command below with your own information. You can also remove the --output table option to view more information about your connections.
az aks connection list --resource-group <cluster-resource-group> --name <cluster-name> --output table
The output also displays the provisioning state of your connections.