Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
A condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control. For example, you can add a condition that requires an object to have a specific tag to read the object. This article describes the format and syntax of role assignment conditions.
Condition format
To better understand role assignment conditions, it helps to look at the format.
Simple condition
The most basic condition consists of a targeted action and an expression. An action is an operation that a user can perform on a resource type. An expression is a statement that evaluates to true or false, which determines whether the action is allowed to be performed.
The following shows the format of a simple condition.

(
(
!(ActionMatches{'<action>'})
)
OR
(
<attribute> <operator> <value>
)
)
The following condition has an action of "Read a blob". The expression checks whether the container name is blobs-example-container.
(
(
!(ActionMatches{'Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read'})
)
OR
(
@Resource[Microsoft.Storage/storageAccounts/blobServices/containers:name]
StringEquals 'blobs-example-container'
)
)
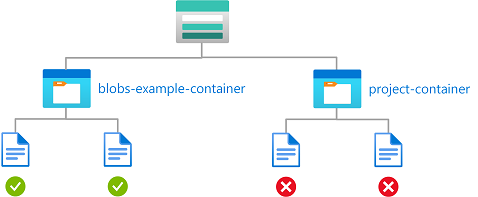
How a condition is evaluated
If a user tries to perform an action in the role assignment that is not <action>, !(ActionMatches) evaluates to true and the overall condition evaluates to true to allow the action to be performed.
If a user tries to perform <action> in the role assignment, !(ActionMatches) evaluates to false, so the expression is evaluated. If the expression evaluates to true, the overall condition evaluates to true to allow <action> to be performed. Otherwise, <action> is not allowed to be performed.
The following pseudo code shows another way that you can read this condition.
if a user tries to perform an action in the role assignment that does not match <action>
{
Allow action to be performed
}
else
{
if <attribute> <operator> <value> is true
{
Allow <action> to be performed
}
else
{
Do not allow <action> to be performed
}
}
Suboperations
Some actions have suboperations. For example, the Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read data action has the suboperation "List blobs". Conditions with suboperations have the following format.

(
(
!(ActionMatches{'<action>'}
AND
SubOperationMatches{'<subOperation>'})
)
OR
(
<attribute> <operator> <value>
)
)
Multiple actions
A condition can include multiple actions that you want to allow if the condition is true. If you select multiple actions for a single condition, there might be fewer attributes to choose from for your condition because the attributes must be available across the selected actions.

(
(
!(ActionMatches{'<action>'})
AND
!(ActionMatches{'<action>'})
)
OR
(
<attribute> <operator> <value>
)
)
Multiple expressions
A condition can include multiple expressions. Depending on the operator, attributes can be checked against multiple values.

(
(
!(ActionMatches{'<action>'})
)
OR
(
<attribute> <operator> <value>
AND | OR
<attribute> <operator> {<value>, <value>, <value>}
AND | OR
<attribute> <operator> <value>
)
)
Multiple conditions
You can also combine conditions to target multiple actions.
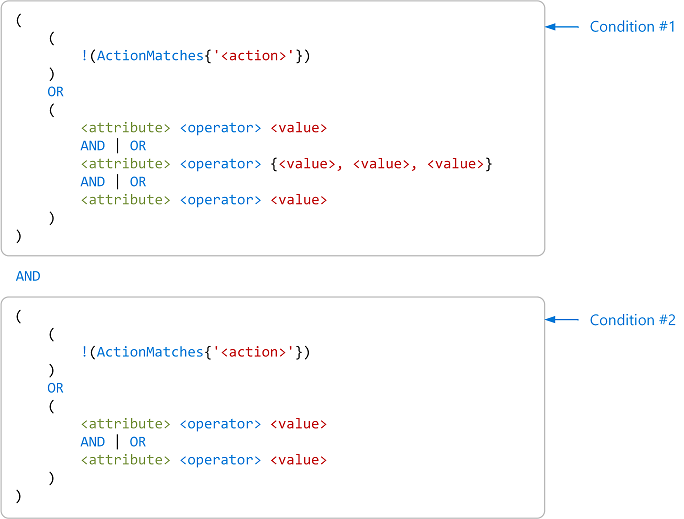
(
(
!(ActionMatches{'<action>'})
)
OR
(
<attribute> <operator> <value>
AND | OR
<attribute> <operator> {<value>, <value>, <value>}
AND | OR
<attribute> <operator> <value>
)
)
AND
(
(
!(ActionMatches{'<action>'})
)
OR
(
<attribute> <operator> <value>
AND | OR
<attribute> <operator> <value>
)
)
Condition syntax
The following shows the syntax for a role assignment condition.
(
(
!(ActionMatches{'<action>'} AND SubOperationMatches{'<subOperation>'})
AND
!(ActionMatches{'<action>'} AND SubOperationMatches{'<subOperation>'})
AND
...
)
OR
(
<attribute> <operator> {<value, <value>, ...}
AND | OR
<attribute> <operator> {<value>, <value>, ...}
AND | OR
...
)
)
AND
(
(
!(ActionMatches{'<action>'} AND SubOperationMatches{'<subOperation>'})
AND
!(ActionMatches{'<action>'} AND SubOperationMatches{'<subOperation>'})
AND
...
)
OR
(
<attribute> <operator> {<value, <value>, ...}
AND | OR
<attribute> <operator> {<value>, <value>, ...}
AND | OR
...
)
)
AND
...
Actions
Currently, conditions can be added to built-in or custom role assignments that have blob storage or queue storage data actions. These include the following built-in roles:
- Storage Blob Data Contributor
- Storage Blob Data Owner
- Storage Blob Data Reader
- Storage Queue Data Contributor
- Storage Queue Data Message Processor
- Storage Queue Data Message Sender
- Storage Queue Data Reader
For a list of the storage actions you can use in conditions, see:
- Actions and attributes for Azure role assignment conditions for Azure Blob Storage
- Actions and attributes for Azure role assignment conditions for Azure Queue Storage.
Attributes
Depending on the selected actions, the attribute might be found in different places. If you select multiple actions for a single condition, there might be fewer attributes to choose from for your condition because the attributes must be available across all of the selected actions. To specify an attribute, you must include the source as a prefix.
| Attribute source | Description | Code |
|---|---|---|
| Environment | Attribute is associated with the environment of the request, such as the network origin of the request or the current date and time. |
@Environment |
| Principal | Attribute is a custom security attribute assigned to the principal, such as a user or enterprise application (service principal). | @Principal |
| Request | Attribute is part of the action request, such as setting the blob index tag. | @Request |
| Resource | Attribute is a property of the resource, such as a container name. | @Resource |
For a complete list of the storage attributes you can use in conditions, see:
Environment attributes
Environment attributes are associated with the circumstances under which the access request is made, such as the date and time of day or the network environment. The network environment might be whether access is over a specific private endpoint or a virtual network subnet, or perhaps over any private link.
The following table lists the supported environment attributes for conditions.
| Display name | Description | Attribute | Type |
|---|---|---|---|
| Is private link1 | Use this attribute in conditions to require access over any private link. | isPrivateLink |
Boolean |
| Private endpoint1,2 | Use this attribute in conditions to restrict access over a specific private endpoint. | Microsoft.Network/privateEndpoints |
String |
| Subnet1,3 | Use this attribute in conditions to restrict access from a specific subnet. | Microsoft.Network/virtualNetworks/subnets |
String |
| UTC now | Use this attribute in conditions to restrict access to objects during specific time periods. | UtcNow |
DateTime |
1 For copy operations, the Is private link, Private endpoint, and Subnet attributes only apply to the destination, such a storage account, not the source. For more information about the copy operations this applies to, select each attribute in the table to see more details.
2 You can only use the Private endpoint attribute if you currently have at least one private endpoint configured in your subscription.
3 You can only use the Subnet attribute if you currently have at least one virtual network subnet using service endpoints configured in your subscription.
Principal attributes
Principal attributes are custom security attributes assigned to the security principal requesting access to a resource. The security principal can be a user or an enterprise application (service principal).
To use principal attributes, you must have the following:
- Microsoft Entra permissions for the signed-in user, such as the Attribute Assignment Administrator role
- Custom security attributes defined in Microsoft Entra ID
For more information about custom security attributes, see:
- Add or deactivate custom security attributes in Microsoft Entra ID
- Allow read access to blobs based on tags and custom security attributes
- Principal does not appear in Attribute source
Request attributes
Request attributes are associated with the criteria specified in an access request, such as the specified prefix of blobs to be listed.
Resource attributes
Resource attributes are associated with the object to which access is being requested, such as the storage account name, container name, or whether hierarchical namespace is enabled for the storage account.
Function operators
This section lists the function operators that are available to construct conditions.
ActionMatches
| Property | Value |
|---|---|
| Operator | ActionMatches |
| Description | Checks if the current action matches the specified action pattern. |
| Examples | ActionMatches{'Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read'}If the action being checked equals "Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read", then true ActionMatches{'Microsoft.Authorization/roleAssignments/*'}If the action being checked equals "Microsoft.Authorization/roleAssignments/write", then true ActionMatches{'Microsoft.Authorization/roleDefinitions/*'}If the action being checked equals "Microsoft.Authorization/roleAssignments/write", then false |
SubOperationMatches
| Property | Value |
|---|---|
| Operator | SubOperationMatches |
| Description | Checks if the current suboperation matches the specified suboperation pattern. |
| Examples | SubOperationMatches{'Blob.List'} |
Exists
| Property | Value |
|---|---|
| Operator | Exists |
| Description | Checks if the specified attribute exists. |
| Examples | Exists @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:snapshot] |
| Attributes support 1 | Encryption scope name Snapshot Version ID |
1 The Exists operator is supported for only these attributes in the visual ABAC condition builder in the Azure portal. You can add the Exists operator to any attribute using other tools, such as PowerShell, the Azure CLI, the REST API, and the condition code editor in the Azure portal.
Logical operators
This section lists the logical operators that are available to construct conditions.
And
| Property | Value |
|---|---|
| Operators | AND&& |
| Description | And operator. |
| Examples | !(ActionMatches{'Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read'} AND NOT SubOperationMatches{'Blob.List'}) |
Or
| Property | Value |
|---|---|
| Operators | OR|| |
| Description | Or operator. |
| Examples | @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:versionId] DateTimeEquals '2022-06-01T00:00:00.0Z' OR NOT Exists @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:versionId |
Not
| Property | Value |
|---|---|
| Operators | NOT! |
| Description | Not or negation operator. |
| Examples | NOT Exists @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:versionId] |
Boolean comparison operators
This section lists the Boolean comparison operators that are available to construct conditions.
| Property | Value |
|---|---|
| Operators | BoolEqualsBoolNotEquals |
| Description | Boolean comparison. |
| Examples | @Resource[Microsoft.Storage/storageAccounts:isHnsEnabled] BoolEquals true |
String comparison operators
This section lists the string comparison operators that are available to construct conditions.
StringEquals
| Property | Value |
|---|---|
| Operators | StringEqualsStringEqualsIgnoreCase |
| Description | Case-sensitive (or case-insensitive) matching. The values must exactly match the string. |
| Examples | @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs/tags:Project<$key_case_sensitive$>] StringEquals 'Cascade' |
StringNotEquals
| Property | Value |
|---|---|
| Operators | StringNotEqualsStringNotEqualsIgnoreCase |
| Description | Negation of StringEquals (or StringEqualsIgnoreCase) operator. |
StringStartsWith
| Property | Value |
|---|---|
| Operators | StringStartsWithStringStartsWithIgnoreCase |
| Description | Case-sensitive (or case-insensitive) matching. The values start with the string. |
StringNotStartsWith
| Property | Value |
|---|---|
| Operators | StringNotStartsWithStringNotStartsWithIgnoreCase |
| Description | Negation of StringStartsWith (or StringStartsWithIgnoreCase) operator. |
StringLike
| Property | Value |
|---|---|
| Operators | StringLikeStringLikeIgnoreCase |
| Description | Case-sensitive (or case-insensitive) matching. The values can include a multi-character match wildcard (*) or a single-character match wildcard (?) anywhere in the string. If needed, these characters can be escaped by add a backslash \* and \?. |
| Examples | @Resource[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:path] StringLike 'readonly/*'Resource[name1] StringLike 'a*c?'If Resource[name1] equals "abcd", then true Resource[name1] StringLike 'A*C?'If Resource[name1] equals "abcd", then false Resource[name1] StringLike 'a*c'If Resource[name1] equals "abcd", then false |
StringNotLike
| Property | Value |
|---|---|
| Operators | StringNotLikeStringNotLikeIgnoreCase |
| Description | Negation of StringLike (or StringLikeIgnoreCase) operator. |
Numeric comparison operators
This section lists the numeric comparison operators that are available to construct conditions.
| Property | Value |
|---|---|
| Operators | NumericEqualsNumericNotEqualsNumericGreaterThanNumericGreaterThanEqualsNumericLessThanNumericLessThanEquals |
| Description | Number matching. Only integers are supported. |
DateTime comparison operators
This section lists the date/time comparison operators that are available to construct conditions.
| Property | Value |
|---|---|
| Operators | DateTimeEqualsDateTimeNotEqualsDateTimeGreaterThanDateTimeGreaterThanEqualsDateTimeLessThanDateTimeLessThanEquals |
| Description | Full-precision check with the format: yyyy-mm-ddThh:mm:ss.mmmmmmmZ. Used for blob version ID, blob snapshot, and UTC now. |
| Examples | @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs:versionId] DateTimeEquals '2022-06-01T00:00:00.0Z' |
GUID comparison operators
This section lists the globally unique identifier (GUID) comparison operators that are available to construct conditions.
| Property | Value |
|---|---|
| Operators | GuidEqualsGuidNotEquals |
| Description | Case-insensitive matching with the format: 00000000-0000-0000-0000-000000000000. Used to identify a resource, such as principal ID or role definition ID. |
| Examples |
Cross product comparison operators
This section lists the cross product comparison operators that are available to construct conditions.
ForAnyOfAnyValues
| Property | Value |
|---|---|
| Operators | ForAnyOfAnyValues:StringEqualsForAnyOfAnyValues:StringEqualsIgnoreCaseForAnyOfAnyValues:StringNotEqualsForAnyOfAnyValues:StringNotEqualsIgnoreCaseForAnyOfAnyValues:StringLikeForAnyOfAnyValues:StringLikeIgnoreCaseForAnyOfAnyValues:StringNotLikeForAnyOfAnyValues:StringNotLikeIgnoreCaseForAnyOfAnyValues:NumericEqualsForAnyOfAnyValues:NumericNotEqualsForAnyOfAnyValues:NumericGreaterThanForAnyOfAnyValues:NumericGreaterThanEqualsForAnyOfAnyValues:NumericLessThanForAnyOfAnyValues:NumericLessThanEqualsForAnyOfAnyValues:GuidEqualsForAnyOfAnyValues:GuidNotEquals |
| Description | If at least one value on the left-hand side satisfies the comparison to at least one value on the right-hand side, then the expression evaluates to true. Has the format: ForAnyOfAnyValues:<BooleanFunction>. Supports multiple strings and numbers. |
| Examples | @Resource[Microsoft.Storage/storageAccounts/encryptionScopes:name] ForAnyOfAnyValues:StringEquals {'validScope1', 'validScope2'}If encryption scope name equals validScope1 or validScope2, then true.{'red', 'blue'} ForAnyOfAnyValues:StringEquals {'blue', 'green'}true {'red', 'blue'} ForAnyOfAnyValues:StringEquals {'orange', 'green'}false |
ForAllOfAnyValues
| Property | Value |
|---|---|
| Operators | ForAllOfAnyValues:StringEqualsForAllOfAnyValues:StringEqualsIgnoreCaseForAllOfAnyValues:StringNotEqualsForAllOfAnyValues:StringNotEqualsIgnoreCaseForAllOfAnyValues:StringLikeForAllOfAnyValues:StringLikeIgnoreCaseForAllOfAnyValues:StringNotLikeForAllOfAnyValues:StringNotLikeIgnoreCaseForAllOfAnyValues:NumericEqualsForAllOfAnyValues:NumericNotEqualsForAllOfAnyValues:NumericGreaterThanForAllOfAnyValues:NumericGreaterThanEqualsForAllOfAnyValues:NumericLessThanForAllOfAnyValues:NumericLessThanEqualsForAllOfAnyValues:GuidEqualsForAllOfAnyValues:GuidNotEquals |
| Description | If every value on the left-hand side satisfies the comparison to at least one value on the right-hand side, then the expression evaluates to true. Has the format: ForAllOfAnyValues:<BooleanFunction>. Supports multiple strings and numbers. |
| Examples | @Request[Microsoft.Storage/storageAccounts/blobServices/containers/blobs/tags:Project<$key_case_sensitive$>] ForAllOfAnyValues:StringEquals {'Cascade', 'Baker', 'Skagit'}{'red', 'blue'} ForAllOfAnyValues:StringEquals {'orange', 'red', 'blue'}true {'red', 'blue'} ForAllOfAnyValues:StringEquals {'red', 'green'}false |
ForAnyOfAllValues
| Property | Value |
|---|---|
| Operators | ForAnyOfAllValues:StringEqualsForAnyOfAllValues:StringEqualsIgnoreCaseForAnyOfAllValues:StringNotEqualsForAnyOfAllValues:StringNotEqualsIgnoreCaseForAnyOfAllValues:StringLikeForAnyOfAllValues:StringLikeIgnoreCaseForAnyOfAllValues:StringNotLikeForAnyOfAllValues:StringNotLikeIgnoreCaseForAnyOfAllValues:NumericEqualsForAnyOfAllValues:NumericNotEqualsForAnyOfAllValues:NumericGreaterThanForAnyOfAllValues:NumericGreaterThanEqualsForAnyOfAllValues:NumericLessThanForAnyOfAllValues:NumericLessThanEqualsForAnyOfAllValues:GuidEqualsForAnyOfAllValues:GuidNotEquals |
| Description | If at least one value on the left-hand side satisfies the comparison to every value on the right-hand side, then the expression evaluates to true. Has the format: ForAnyOfAllValues:<BooleanFunction>. Supports multiple strings and numbers. |
| Examples | {10, 20} ForAnyOfAllValues:NumericLessThan {15, 18}true |
ForAllOfAllValues
| Property | Value |
|---|---|
| Operators | ForAllOfAllValues:StringEqualsForAllOfAllValues:StringEqualsIgnoreCaseForAllOfAllValues:StringNotEqualsForAllOfAllValues:StringNotEqualsIgnoreCaseForAllOfAllValues:StringLikeForAllOfAllValues:StringLikeIgnoreCaseForAllOfAllValues:StringNotLikeForAllOfAllValues:StringNotLikeIgnoreCaseForAllOfAllValues:NumericEqualsForAllOfAllValues:NumericNotEqualsForAllOfAllValues:NumericGreaterThanForAllOfAllValues:NumericGreaterThanEqualsForAllOfAllValues:NumericLessThanForAllOfAllValues:NumericLessThanEqualsForAllOfAllValues:GuidEqualsForAllOfAllValues:GuidNotEquals |
| Description | If every value on the left-hand side satisfies the comparison to every value on the right-hand side, then the expression evaluates to true. Has the format: ForAllOfAllValues:<BooleanFunction>. Supports multiple strings and numbers. |
| Examples | {10, 20} ForAllOfAllValues:NumericLessThan {5, 15, 18}false {10, 20} ForAllOfAllValues:NumericLessThan {25, 30}true {10, 20} ForAllOfAllValues:NumericLessThan {15, 25, 30}false |
Special characters
| Character | Description |
|---|---|
* |
An asterisk (*) represents a multi-character wildcard match that can be used with Like operators. If needed, you can escape an asterisk by adding a backslash \*. |
? |
A question mark (?) represents a single-character wildcard match that can be used with Like operators. If needed, you can escape a question mark by adding a backslash \?. |
$ |
A dollar sign ($) is used to help delineate tag keys. In Azure PowerShell, if a string enclosed in double quotes (") includes a dollar sign, you must prefix it with a backtick (`). For example: tags:Project<`$key_case_sensitive`$>. |
Grouping and precedence
If you have three or more expressions for a targeted action with different operators between the expressions, the evaluation order is ambiguous. You use parentheses () to group expressions and specify the order that the expressions are evaluated. Expressions enclosed in parentheses have higher precedence. For example, if you have the following expression:
a AND b OR c
You must add parentheses in one of the following ways:
(a AND b) OR c
a AND (b OR c)