Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
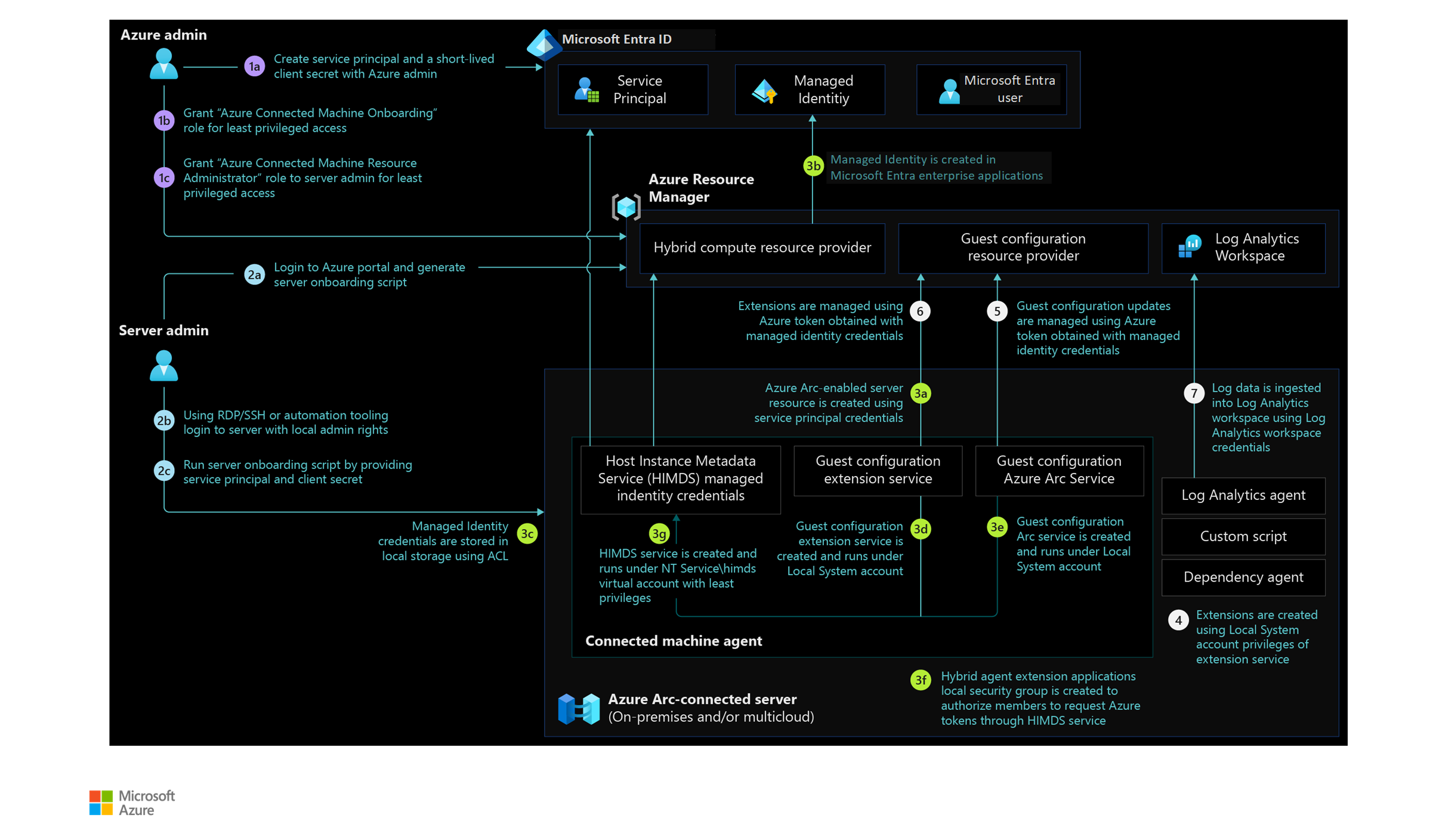
This article provides actionable guidance to secure Azure Arc-enabled servers through proper identity and access management. You learn to configure managed identities, implement role-based access controls, and deploy service principals securely to protect your hybrid infrastructure. Identity management systems are critical for securing Azure Arc-enabled servers. The following reference architecture shows how identities, roles, and permissions work together:
Configure managed identities
System-assigned managed identities provide secure authentication for Azure Arc-enabled servers without storing credentials. The Azure Connected Machine agent creates these identities automatically during server onboarding, but they have no permissions by default and require explicit Azure RBAC role assignments to access Azure resources.
Tip
Start here: If you're new to managed identities, review the managed identity authentication guide for step-by-step implementation instructions.
Identify legitimate use cases for managed identity access. Applications on your servers need specific access tokens to call Azure resources like Key Vault or Storage. Plan access control for these resources before granting permissions to avoid security gaps.
Control privileged user access to managed identity endpoints. Members of local administrators or the Hybrid Agent Extensions Applications group on Windows and the himds group on Linux can request access tokens. Limit membership in these groups to prevent unauthorized access to Azure resources.
Implement role-based access control for managed identities. Use Azure RBAC to grant only the minimum required permissions to managed identities. Perform periodic access reviews to ensure permissions remain appropriate and remove unused access.
Apply role-based access control
Role-based access control limits user privileges and reduces security risks. Users with broad roles like Contributor or Owner can deploy extensions and gain administrative access to Azure Arc-enabled servers, creating potential security vulnerabilities.
Warning
Security risk: Avoid granting broad permissions like Owner or Contributor roles for Arc server access. These roles can provide root-level access to your servers through extension deployment.
Apply the least privilege principle to role assignments. Users, groups, and applications should receive only the minimum permissions needed for their tasks. Roles like Contributor, Owner, or Azure Connected Machine Resource Administrator grant extensive access that can effectively delegate root access to servers.
Use the Azure Connected Machine Onboarding role for server registration. This role allows users to onboard servers to Azure Arc without granting broader management permissions. The role provides only the permissions needed to create and read Arc resources, not to manage extensions or delete servers.
Secure access to monitoring data. Read access to Azure Arc-enabled servers can expose log data collected by the Log Analytics agent. Apply RBAC controls to Log Analytics workspaces to limit who can view sensitive operational data.
Also consider the sensitive data that might be sent to the Azure Monitor Log Analytics workspace; apply the same RBAC principle to the data itself. Read access to Azure Arc-enabled servers can provide access to log data collected by the Log Analytics agent and stored in the associated Log Analytics workspace.
Tip
Learn how to implement granular workspace access controls in the Azure Monitor Logs deployment guide to secure your monitoring data.
Plan identity and access responsibilities
Organizational clarity prevents security gaps and operational conflicts. Clear role definitions ensure the right people have appropriate access to onboard and manage Azure Arc-enabled servers.
- Who can onboard new servers to Azure Arc?
- Who manages servers after they're onboarded?
- What Azure permissions do these roles need?
- How will you separate onboarding from ongoing management?
Define server onboarding responsibilities. Identify who can onboard servers and set required permissions on both the servers and in Azure. This role requires local administrator access on servers and appropriate Azure permissions.
Assign ongoing management responsibilities. Determine who manages Azure Arc-enabled servers after onboarding and who can view operational data from Azure services. Separate these responsibilities based on operational needs and security requirements.
Plan service principal distribution. Create multiple Arc onboarding service principals when different business teams own and operate server groups. Scope each principal to the minimum required resource groups to limit potential security exposure.
Assess enterprise-scale impact. Review the identity and access management design area to understand how Azure Arc-enabled servers integrate with your overall Azure landing zone identity strategy.
Important
Proper role separation is essential for security. Consider your organization's structure when assigning onboarding vs. management responsibilities.
Implement security controls
Security controls protect Azure Arc-enabled servers and the resources they can access. Proper implementation reduces attack surface and ensures compliance with security policies.
Configure secure server onboarding. Use security groups to assign local administrator rights to identified users or service accounts for Azure Arc onboarding at scale. This approach provides consistent access control across your server fleet.
Certificate-based authentication (Recommended)
Deploy service principals with certificates. Use a Microsoft Entra service principal with certificate authentication for server onboarding. Certificates are the recommended authentication method over client secrets because they provide stronger security, support conditional access policies, and reduce credential exposure risk. Scope each principal to the minimum required resource group or subscription.
Alternative authentication methods
Secure client secrets when certificates are not available. If you use client secrets for service principals, make them short-lived, rotate them regularly, and restrict the principal's scope and permissions to reduce security exposure.
Role assignments and access control
Apply appropriate role assignments. Assign the Azure Connected Machine Onboarding role at the resource group level for onboarding operations. Grant the Azure Connected Machine Resource Administrator role to teams who manage server resources in Azure.
Control managed identity access. Use managed identities for applications on servers to access Microsoft Entra protected resources. Restrict access to only authorized applications using Microsoft Entra application permissions.
Manage local access to identity endpoints. Use the
Hybrid agent extension applicationssecurity group on Windows or the himds group on Linux to control which users can request Azure resource access tokens from Arc-enabled servers.
Note
Ready to implement these security controls? Start with the Azure Arc-enabled servers prerequisites to ensure your environment is properly configured.
Azure tools and resources
This comprehensive reference helps you implement identity and access management for Azure Arc-enabled servers. Use these tools to configure secure authentication, role-based access control, and monitoring.
| Category | Tool | Description | Quick Start |
|---|---|---|---|
| Identity | Microsoft Entra managed identities | Provides secure authentication for applications without storing credentials | Configure managed identity access |
| Security | Azure Role-Based Access Control | Controls access to resources based on least privilege principle | Assign RBAC roles |
| Onboarding | Microsoft Entra service principal | Enables automated server onboarding at scale | Create service principal |
| Security | Azure Arc-enabled servers security overview | Comprehensive security guidance for Arc-enabled servers | Review security controls |
| Monitoring | Azure Monitor Logs deployment guide | Implements granular access control for log data | Configure workspace access |
| Architecture | Identity and access management design area | Enterprise-scale landing zone identity guidance | Review design principles |
| Permissions | Microsoft Entra application permissions | Controls application access to managed identities | Configure app permissions |
| Prerequisites | Azure Arc-enabled servers prerequisites | Requirements for deploying Arc-enabled servers | Check prerequisites |
| Deployment | At-scale deployment planning | Guidance for large-scale Arc server deployments | Plan your deployment |
| Learning | Azure Arc learning path | Comprehensive training for Azure Arc management | Start learning module |
Next steps
Ready to secure your Azure Arc environment? Continue with network security configuration to complete your hybrid infrastructure protection:
Continue your Azure Arc journey
| Topic | Description | Action |
|---|---|---|
| Network Security | Secure network connectivity and topology | Configure Arc networking |
| Deployment Planning | Plan large-scale Arc server deployment | Review deployment guide |
| Hands-on Learning | Build practical Arc management skills | Start learning path |
| Security Baseline | Implement comprehensive security controls | Apply security baseline |