Hello,
Hoping someone can help clarify something for me.
I am looking to setup WDAC for cloud (AAD/Intune) managed Windows 11 devices and would like to use the 'managed installer' feature to automatically allow applications which are deployed via Intune.
I have been following the MS guidance as set out in the link below to create the required supporting AppLocker policy:
https://free.blessedness.top/en-us/windows/security/threat-protection/windows-defender-application-control/configure-authorized-apps-deployed-with-a-managed-installer#create-and-deploy-an-applocker-policy-that-defines-your-managed-installer-rules-and-enables-services-enforcement-for-executables-and-dlls
Whilst this appears to work (I can for example install and run a given app from Intune, but not manually), I notice that it results in pretty much every DLL execution being logged with event ID 8003 in the Microsoft-Windows-AppLocker/EXE and DLL log.
This is creating an excessive amount of logging activity and whilst I can kind of see why, given the auditonly setting in the applocker policy I am not convinced it is correct/expected.
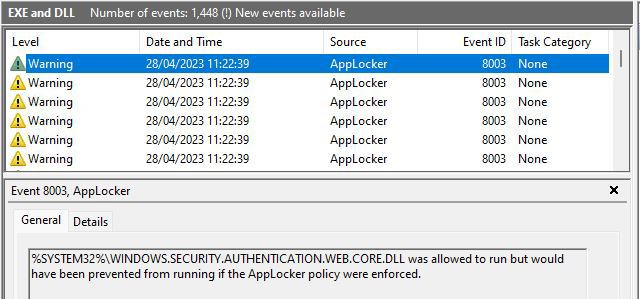
Please could someone clarify?
Is this expected?
Does anyone have WDAC working with the managed installer option and do they see the same?
Put simply, I guess my question is, would using the WDAC with the managed installer option be expected to create excessive logging of DLL audit events in the log?
Many thanks,
Phil
